About the CoMSES Model Library more info
Our mission is to help computational modelers develop, document, and share their computational models in accordance with community standards and good open science and software engineering practices. Model authors can publish their model source code in the Computational Model Library with narrative documentation as well as metadata that supports open science and emerging norms that facilitate software citation, computational reproducibility / frictionless reuse, and interoperability. Model authors can also request private peer review of their computational models. Models that pass peer review receive a DOI once published.
All users of models published in the library must cite model authors when they use and benefit from their code.
Please check out our model publishing tutorial and feel free to contact us if you have any questions or concerns about publishing your model(s) in the Computational Model Library.
We also maintain a curated database of over 7500 publications of agent-based and individual based models with detailed metadata on availability of code and bibliometric information on the landscape of ABM/IBM publications that we welcome you to explore.
Displaying 10 of 549 results for "Niklas Hase" clear search
A basic macroeconomic agent-based model for analyzing monetary regime shifts
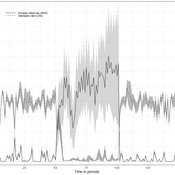
Oliver Reinhardt Florian Peters Doris Neuberger Adelinde Uhrmacher | Published Tuesday, May 03, 2022In macroeconomics, an emerging discussion of alternative monetary systems addresses the dimensions of systemic risk in advanced financial systems. Monetary regime changes with the aim of achieving a more sustainable financial system have already been discussed in several European parliaments and were the subject of a referendum in Switzerland. However, their effectiveness and efficacy concerning macro-financial stability are not well-known. This paper introduces a macroeconomic agent-based model (MABM) in a novel simulation environment to simulate the current monetary system, which may serve as a basis to implement and analyze monetary regime shifts. In this context, the monetary system affects the lending potential of banks and might impact the dynamics of financial crises. MABMs are predestined to replicate emergent financial crisis dynamics, analyze institutional changes within a financial system, and thus measure macro-financial stability. The used simulation environment makes the model more accessible and facilitates exploring the impact of different hypotheses and mechanisms in a less complex way. The model replicates a wide range of stylized economic facts, including simplifying assumptions to reduce model complexity.
An Agent-Based Model of an Insurance Market driven by Supply and Demand with Imperfectly Estimated Strategies in C#
Rei England | Published Sunday, September 24, 2023This is a simulation of an insurance market where the premium moves according to the balance between supply and demand. In this model, insurers set their supply with the aim of maximising their expected utility gain while operating under imperfect information about both customer demand and underlying risk distributions.
There are seven types of insurer strategies. One type follows a rational strategy within the bounds of imperfect information. The other six types also seek to maximise their utility gain, but base their market expectations on a chartist strategy. Under this strategy, market premium is extrapolated from trends based on past insurance prices. This is subdivided according to whether the insurer is trend following or a contrarian (counter-trend), and further depending on whether the trend is estimated from short-term, medium-term, or long-term data.
Customers are modelled as a whole and allocated between insurers according to available supply. Customer demand is calculated according to a logit choice model based on the expected utility gain of purchasing insurance for an average customer versus the expected utility gain of non-purchase.
Peer reviewed A financial market with zero intelligence agents
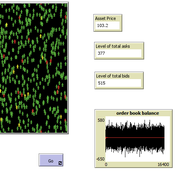
edgarkp | Published Wednesday, March 27, 2024The model’s aim is to represent the price dynamics under very simple market conditions, given the values adopted by the user for the model parameters. We suppose the market of a financial asset contains agents on the hypothesis they have zero-intelligence. In each period, a certain amount of agents are randomly selected to participate to the market. Each of these agents decides, in a equiprobable way, between proposing to make a transaction (talk = 1) or not (talk = 0). Again in an equiprobable way, each participating agent decides to speak on the supply (ask) or the demand side (bid) of the market, and proposes a volume of assets, where this number is drawn randomly from a uniform distribution. The granularity depends on various factors, including market conventions, the type of assets or goods being traded, and regulatory requirements. In some markets, high granularity is essential to capture small price movements accurately, while in others, coarser granularity is sufficient due to the nature of the assets or goods being traded
Peer reviewed An IBM of a fishing fleet exploiting a pelagic resource and with a fisher management system. A preliminary version.
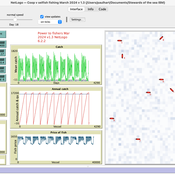
Paul Hart | Published Tuesday, March 19, 2024A fisher directed management system was describeded by Hart (2021). It was proposed that fishers should only be allowed to exploit a resource if they collaborated in a resource management system for which they would own and be collectively responsible for. As part of the system fishers would need to follow the rules of exploitation set by the group and provide a central unit with data with which to monitor the fishery. Any fisher not following the rules would at first be fined but eventually expelled from the fishery if he/she continued to act selfishly. This version of the model establishes the dynamics of a fleet of vessels and controls overfishing by imposing fines on fishers whose income is low and who are tempted to keep fishing beyond the set quota which is established each year depending on the abundance of the fish stock. This version will later be elaborated to have interactions between the fishers including pressure to comply with the norms set by the group and which could lead to a stable management system.
Using Agent-Based Modelling and Reinforcement Learning to Study Hybrid Threats
kpadur | Published Friday, September 20, 2024Hybrid attacks coordinate the exploitation of vulnerabilities across domains to undermine trust in authorities and cause social unrest. Whilst such attacks have primarily been seen in active conflict zones, there is growing concern about the potential harm that can be caused by hybrid attacks more generally and a desire to discover how better to identify and react to them. In addressing such threats, it is important to be able to identify and understand an adversary’s behaviour. Game theory is the approach predominantly used in security and defence literature for this purpose. However, the underlying rationality assumption, the equilibrium concept of game theory, as well as the need to make simplifying assumptions can limit its use in the study of emerging threats. To study hybrid threats, we present a novel agent-based model in which, for the first time, agents use reinforcement learning to inform their decisions. This model allows us to investigate the behavioural strategies of threat agents with hybrid attack capabilities as well as their broader impact on the behaviours and opinions of other agents.
Peer reviewed MicroAnts 2.5
Diogo Alves | Published Thursday, October 16, 2025MicroAnts 2.5 is a general-purpose agent-based model designed as a flexible workhorse for simulating ecological and evolutionary dynamics in artificial populations, as well as, potentially, the emergence of political institutions and economic regimes. It builds on and extends Stephen Wright’s original MicroAnts 2.0 by introducing configurable predators, inequality tracking, and other options.
Ant agents are of two tyes/casts and controlled by 16-bit chromosomes encoding traits such as vision, movement, mating thresholds, sensing, and combat strength. Predators (anteaters) operate in static, random, or targeted predatory modes. Ants reproduce, mutate, cooperate, fight, and die based on their traits and interactions. Environmental pressures (poison and predators) and social dynamics (sharing, mating, combat) drive emergent behavior across red and black ant populations.
The model supports insertion of custom agents at runtime, configurable mutation/inversion rates, and exports detailed statistics, including inequality metrics (e.g., Gini coefficients), trait frequencies, predator kills, and lineage data. Intended for rapid testing and educational experimentation, MicroAnts 2.5 serves as a modular base for more complex ecological and social simulations.
An agent-based approach to weighted decision making in the spatially and temporally variable South African Paleoscape
Colin Wren | Published Thursday, December 29, 2016This model simulates a foraging system based on Middle Stone Age plant and shellfish foraging in South Africa.
COMM-PDND: Communication-Based Model of Perceived Descriptive Norm Dynamics in Digital Networks
Lars Reinelt | Published Friday, September 08, 2023The Communication-Based Model of Perceived Descriptive Norm Dynamics in Digital Networks (COMM-PDND) is an agent-based model specifically created to examine the dynamics of perceived descriptive norms in the context of digital network structures. The model, developed as part of a master’s thesis titled “The Dynamics of Perceived Descriptive Norms in Digital Network Publics: An Agent-Based Simulation,” emphasizes the critical role of communication processes in norm formation. It focuses on the role of communicative interactions in shaping perceived descriptive norms.
The COMM-PDND is tuned to explore the effects of normative deviance in digital social networks. It provides functionalities for manipulating agents according to their network position, and has a versatile set of customizable parameters, making it adaptable to a wide range of research contexts.
IDEAL
Arika Ligmann-Zielinska | Published Thursday, August 07, 2014IDEAL: Agent-Based Model of Residential Land Use Change where the choice of new residential development in based on the Ideal-point decision rule.
Seasonal Social Networks and Learning Opportunities Under Unbiased Cultural Transmission
Adam Rorabaugh | Published Monday, May 18, 2015This agent-based model examines the impact of seasonal aggregation, dispersion, and learning opportunities on the richness and evenness of artifact styles under random social learning (unbiased transmission).
Displaying 10 of 549 results for "Niklas Hase" clear search